How to Protect Facebook or Twitter from Firesheep Attack
If you have Facebook or Twitter account, then you should read this article to understand an easy way to steal Facebook or Twitter session and ways to protect it.
There is an easy way to use Firefox extension which is called Firesheep to sniff and steal unencrypted cookies of Facebook, Twitter or other major websites. This Firesheep extension works well on Firefox browser version 3.6.13 or 3.6.24, but might not compatible with latest version of Firefox web browser.
How it does the job? Well, after you have installed this extension in Firefox web browser, you just need to open the Firesheep sidebar and click Start Capturing. As many websites only encrypt the network traffic during login process, but then make use of unencrypted connection for user data communication, and so the unencrypted cookies will be easily captured by Firesheep and the session will be hijacked eventually. Once the session is hijacked, Firesheep shows captured credentials (Facebook, Twitter, etc) on a sidebar displayed in the browser, and allows you to instantly take over the hijacked session by double-clicking on the victim’s name.
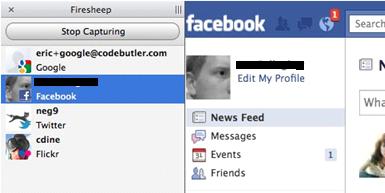
Ok, here comes the important part! Let me show you several ways that you can use to prevent this kind of attack:
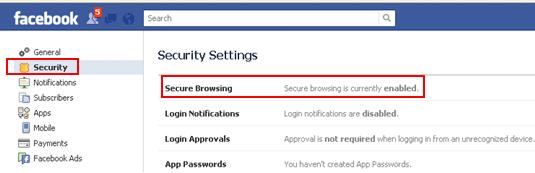
- If you have Facebook account, you should enable Secure Browsing as shown below to encrypt all Facebook network traffic.
Once you have logged in to Facebook, go to Accounts Settings, click Security and finally enable Secure Browsing.
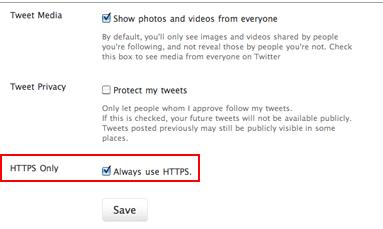
- If you are Twitter user, go to Settings of your profile after logging in to Twitter, check Always use HTTPS option and click Save.
- If you use Firefox or Chrome web browser, you can then install this HTTPS Everywhere extension to encrypt communication with many major websites. Advise you to read its FAQ to get more understanding before installing it.
- You should always connect your laptop or computer to secured public wireless hotspot that requires authentication, so that all network traffic will be encrypted on that connected wireless network.
Recommended Articles:
Wireless Scanning Tool to Identify Interference – inSSIDer
Powerline Ethernet Adapter – Simple Way to Extend Home Network
Quick Tips to Secure Android Smartphone
Return to top of "How to Protect Facebook or Twitter from Firesheep Attack"!!
Enjoy this page? Here's another way to pay it forward...
Would you prefer to share this page with others by linking to it?
- Click on the HTML link code below.
- Copy and paste it, adding a note of your own, into your blog, a Web page, forums, a blog comment, your Facebook account, or anywhere that someone would find this page valuable.



Would you prefer to share this page with others by linking to it?